AWS Identity Center JIT RBAC with Abbey
Modeling Role-Based Access Control in AWS Identity Center using Abbey: A JIT Approach
September 29, 2023 · 6 min read

TL;DR
-
🔒 RBAC is an easy way to organize AWS Identity Center permissions. RBAC is based on group membership.
-
🛠️ Abbey can simplify RBAC management by automating JIT membership and revocation using AWS Identity Center groups.
-
🚀 Define memberships and policies using Abbey and never worry about dangling permissions again.
-
📺 If you want to watch us do RBAC with Identity Center groups, check this Youtube video out
Video
Introduction
Organizing users and permissions in AWS can be confusing. A common way that organizations manage access permissions is using RBAC through the AWS Identity Center. Role-Based Access Control (RBAC) is a method of managing access to systems or network resources based on the roles of individual users within an enterprise. In this context, access is the ability of an individual user to perform a specific task, such as view, create, or modify an AWS Resource. Roles are defined according to job function, authority, and responsibility within the enterprise. Think of a "Prod Access" role, which allows users to have read-only access to production resources. This can be separate from a "BI Read" role that has read-only access to BI tools at the company.
In the AWS Identity Center, RBAC is modeled through the use of groups. These groups represent roles and users are added to these groups. Each group can be configured to grant specific permissions scoped to an AWS account, and we can use group memberships to give users roles. Unfortunately, managing these memberships can be a daunting task, especially in large organizations. This is where Abbey comes in, making it easy to have Just-in-Time (JIT) membership in these groups. Modeling RBAC in AWS Identity Center
In AWS Identity Center, groups are used to model RBAC roles. Each group is associated with a set of permissions that define what actions members of the group can perform. To grant a user a certain role, you simply add them to the corresponding group. For example, you might have a group called "BI Read" that gives read access to BI-related AWS Resources in the BI account. When Alice wants "BI Read" access, we can add Alice to the "BI Read" group.
This is a straightforward and intuitive way to manage access, but it can become cumbersome as your organization grows and you have more users and roles to manage. Keeping track of which users are part of which group can be stressful and most importantly it's easy to keep a user inside a group for much longer than they should be. Sometimes we forget to remove users from a group forever! Some companies use quarterly mandated manual reviews to make sure that groups do not have members who don't need the corresponding access. JIT Membership as a way to give least permissions
One way to avoid having your users hold onto group memberships for too long and to make sure only the users that are needed are added to groups is to use Just-in-Time (JIT) Membership. With JIT membership users are added to groups, assigned RBAC roles, only when the user needs the role. It's tempting to add a gate to this approach: file a ticket for group membership and then once the ticket is closed the user is removed from the group. This leads to both friction for your users, who need to file tickets, and toil for administrators tasked with creating ticket workflows for group removal.
Abbey's Approach
Abbey simplifies this process by enabling JIT membership in AWS Identity Center groups. With Abbey, you don't have to manually add users to groups when they need access. Instead, you can create policies which offer time-based access. After the time expires, their access is automatically removed.
For example, let's say you have a developer who needs temporary access to a BI tool to run some analytics queries. Instead of manually adding them to the "BI Read" group, you can use Abbey to automatically grant them the necessary permissions when they request access. Once they're done, Abbey can automatically remove them from the group, ensuring that they don't retain unnecessary access. Abbey also lets you create policies to do things like offer "BI Read" group membership for only 24 hours. This way there's no toil in granting access and you can rest easy knowing that access is limited to 24 hours. How to Set Up JIT Membership with Abbey Setting up JIT membership with Abbey is a straightforward process. We'll be using the AWS IAM Identity Center Groups example. Here's a step-by-step guide:
- Define your users and groups in AWS Identity Center and Terraform. These groups will represent your RBAC roles.
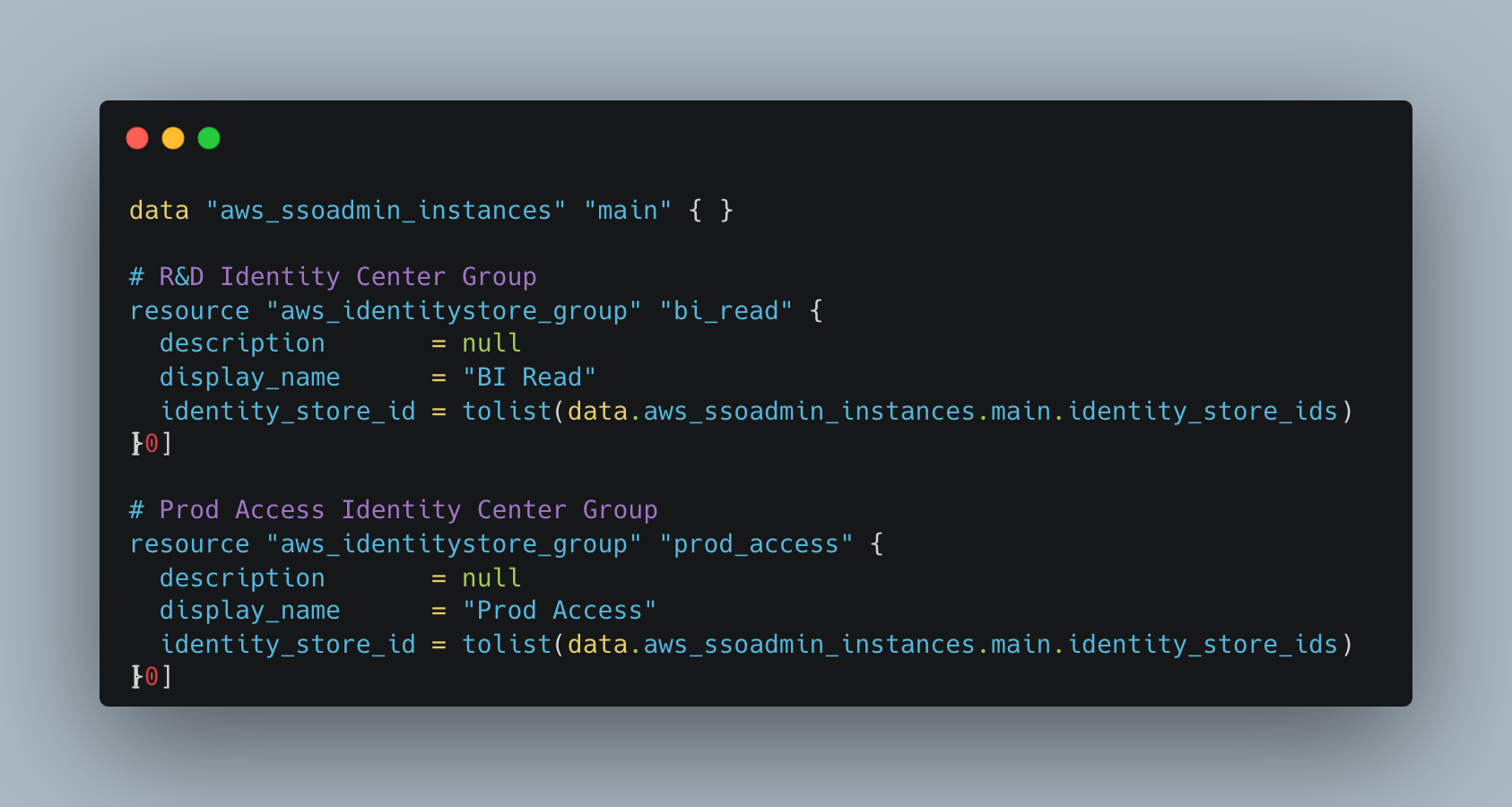
- Define which permissions your groups will grant you in AWS. Once users are added to groups, they will have these AWS IAM Permissions.
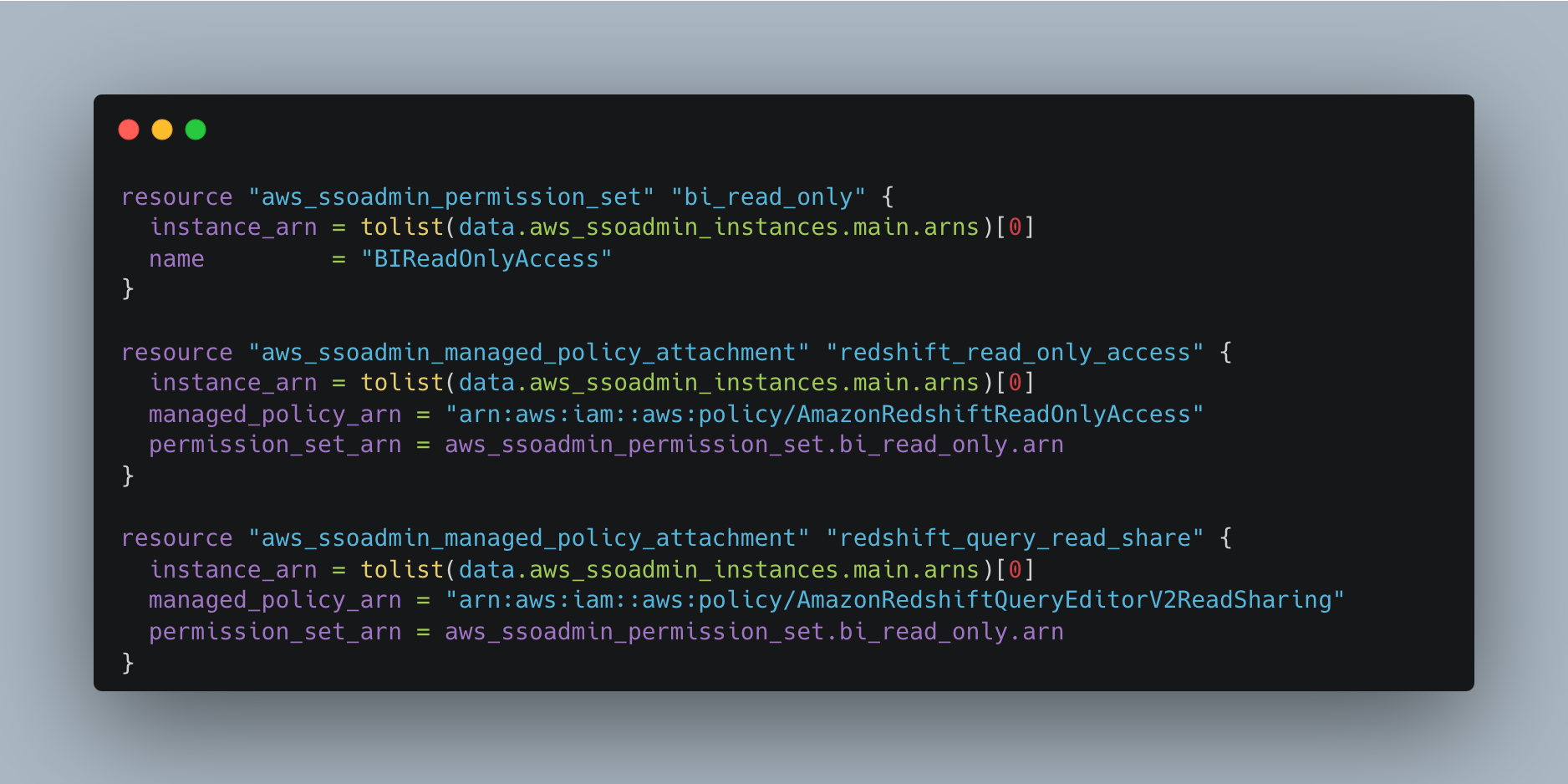
- Create an Abbey resource to manage the group association. When using Abbey, this Terraform resource will be created, tying the user to the group.
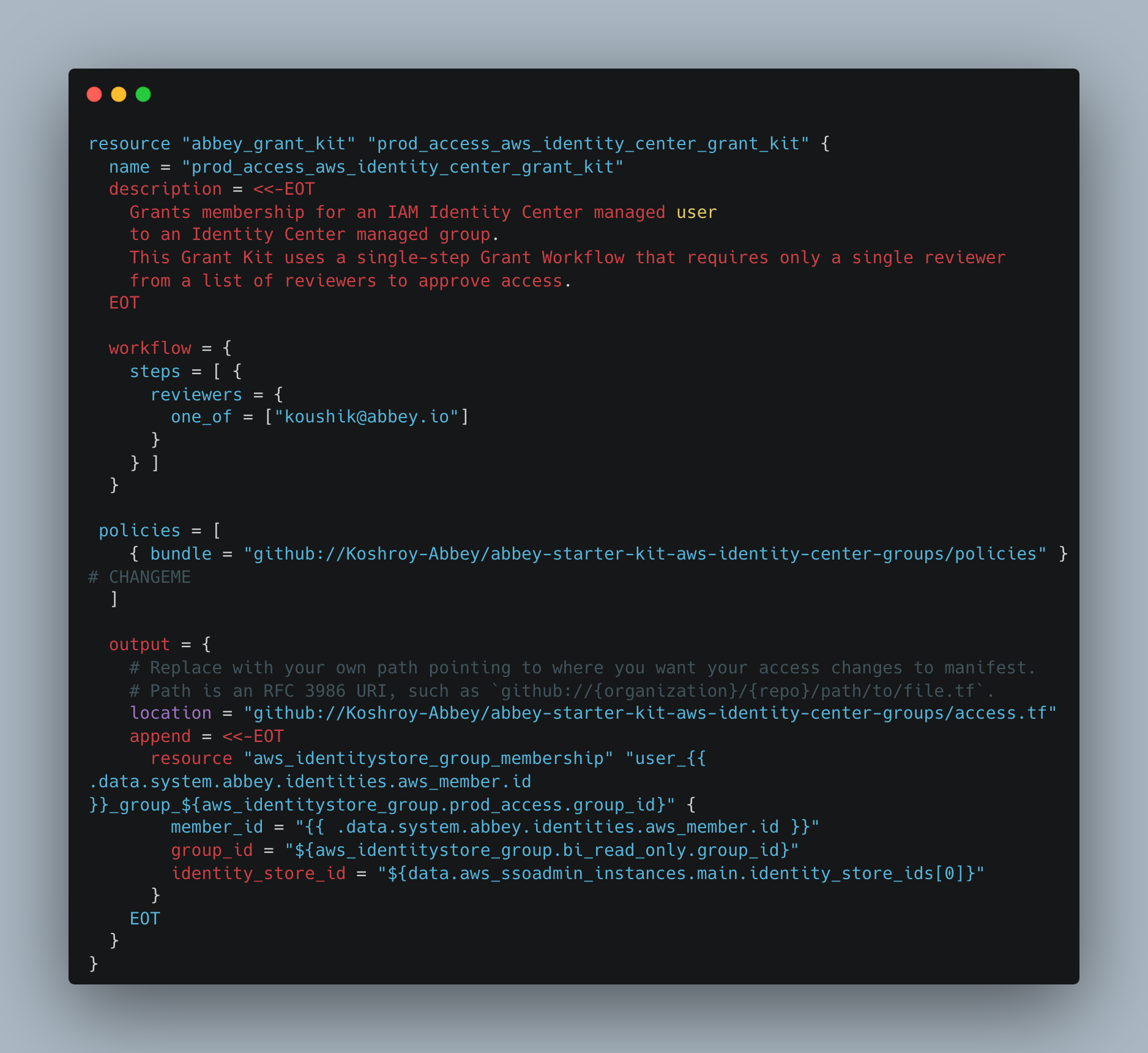
- Create a policy which specifies how long access should be granted for. This example gives access for 24 hours.
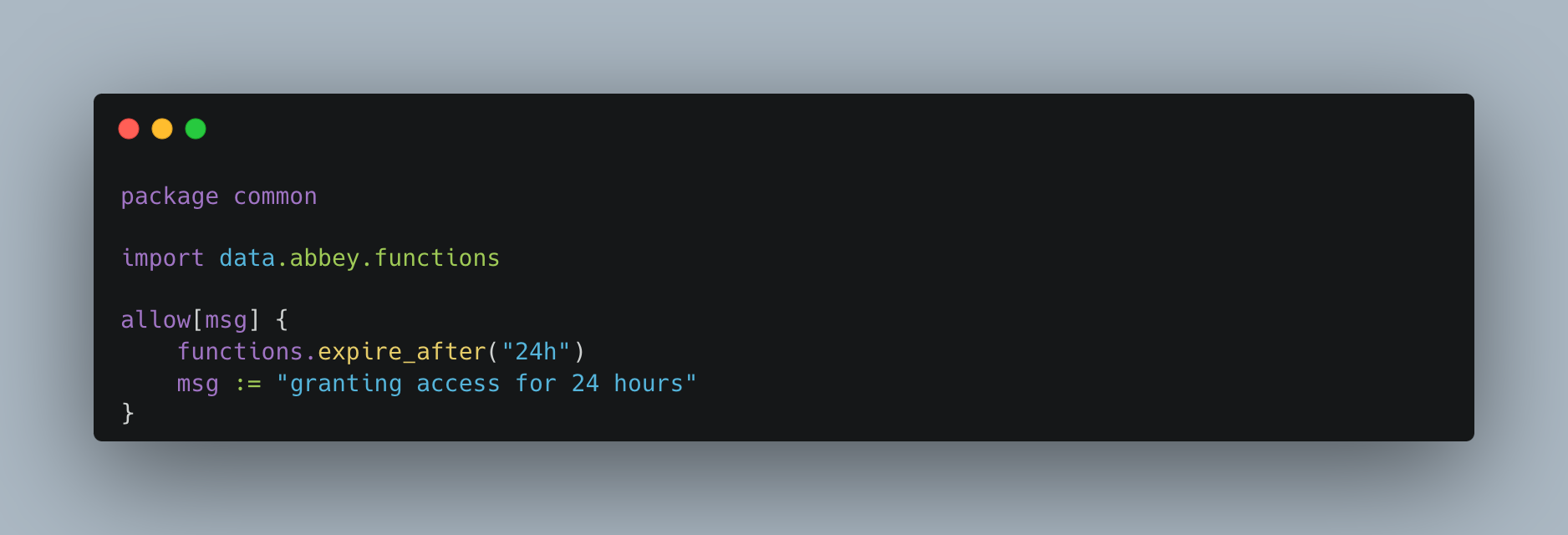
- That's it! Now you can use Abbey to request access to groups and be confident that Abbey will remove access in 24 hours. Abbey will make git commits to your repository so all access are easily tracked through commit history.
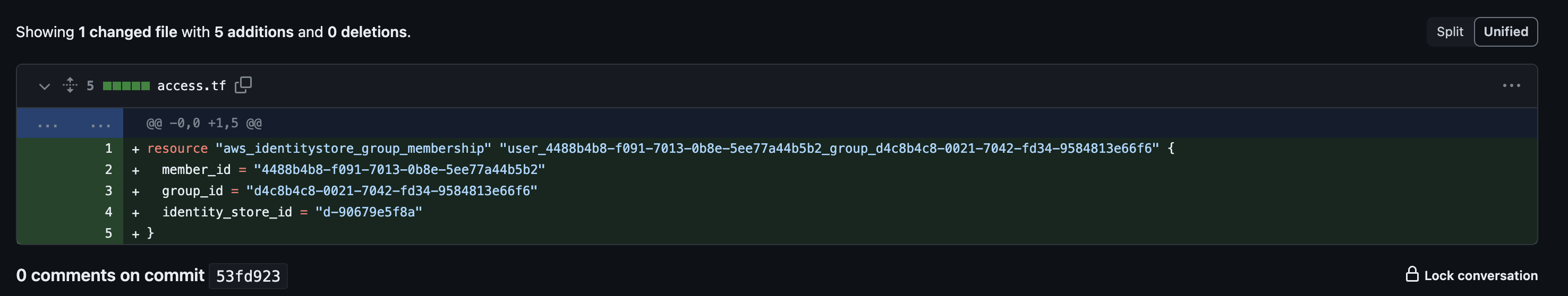
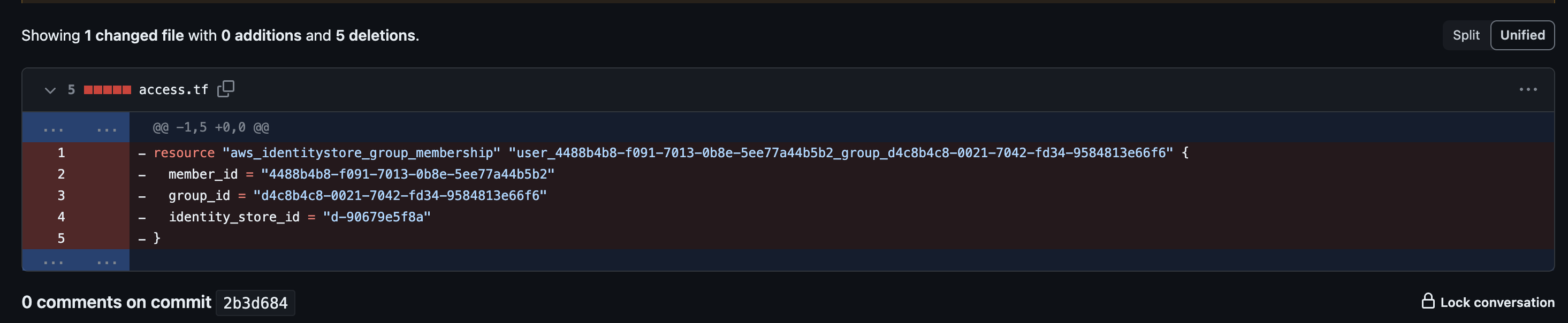
Conclusion
Managing access in a large organization can be a complex task, but tools like Abbey make it easier. By enabling JIT membership in AWS Identity Center groups, Abbey helps you create a streamlined RBAC management system to simplify your access management process, reduce administrative overhead, and improve security. With Abbey, you can focus less on managing access and more on your core business operations.
Automate access management with Terraform today.
Abbey is the easiest way to add automated access request flows to your existing Terraform resources.
Improve security. Reduce toil. Simplify compliance.